USB eToken for Windows domain user RDP Authentication
– Using Safenet USB eToken for Windows Server 2012 domain user remote desktop Authentication
This Safenet USB eToken 5105 key is on loan from vendor for our testing. My testing environment is a windows server 2012 domain built from VMware ESXi 5.1. For the sake for testing remote desktop, I have do Port forward for remote desktop port in domain controllers and client as below , where real-ip is the hostname for the firewall machine in the ESXi evironment :
| Hostname | IP | Remote Desktop |
| DC: server01.domain1.local | 192.168.1.201 | real-ip:3381 |
| DC: server02.domain1.local | 192.168.1.202 | real-ip:3382 |
| Client: client01.domain1.local | 192.168.1.100 | real-ip:3383 |
1. Installation of AD Certificate Service in domain1\server02
2. Configuration of Windows Server 2012 Certificate Authority in domain1\server02
3. Preparation of Safenet USB eToken for domain user authentication
4. Enroll the Enrollment Agent Certificate in domain1\server02
5. Enroll on behalf of …
6. Configuration on remote desktop client (from different windows domains )
My references link are as follows:
– A Complete Guide on Active Directory Certificate Services in Windows Server 2008 R2
– Configure Server 2012 CA for Smartcard Authentication
– Smart card from external source/active directory/remote desktop/user name hints
– HowTo: Disable UPN mapping for SmartCard logon
1. Installation of AD Certificate Service in domain1\server02
Start Server Manager in server02 which is the domain controller in a windows 2012 functional level domain “domain1” and then run “Add Roles and Features Wizard” :
-> Role-based or feature-based installation
-> select “server02.domain1.local”
-> check “Active Directory Certificate Services”
-> Check “Certificate Authority” in Role Services
-> Check “Enterprise CA”
-> Check “Root CA”
-> Check “Create a new private key”
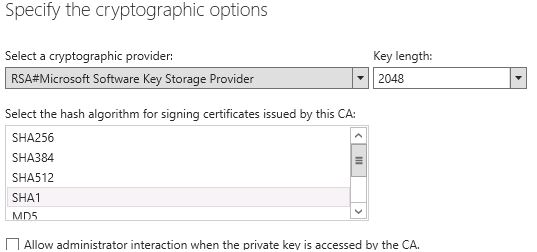
-> Take default for Cryptographic options like below:
-> Choose a common name for this CA , mine: “domain1-SERVER02-CA”
-> Review the installation selections on the confirmation page, as shown below, and click Install.
2. Configuration of Windows Server 2012 Certificate Authority in domain1\server02
After ADCS is installed in domain1\server02, and then proceed to configure the CA :
1. Launch Certification Authority MMC : Server Manager -> Tools -> Certification Authority
2. Click on the ‘Certificate Templates’ node and select Manage
3. Right Click on the ‘Smartcard User’ Certificate Template and then select ‘Duplicate’
4. Change your compatibility settings accordingly, this will depend on your CA infrastructure & End User Devices
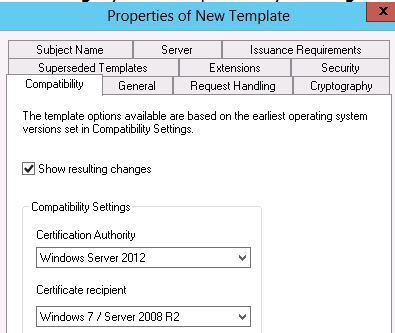
5. Give the new Template an appropriate name, e.g. ‘Smartcard User SEEM’
6. On the Cryptography tab ensure that you select ‘Requests must use one of the following providers’ and then select “eToken Base Cryptographic Provider”
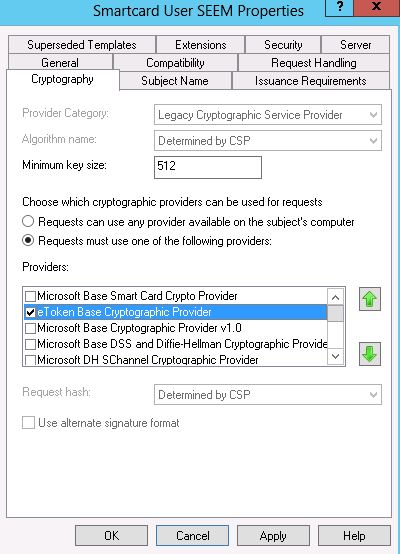
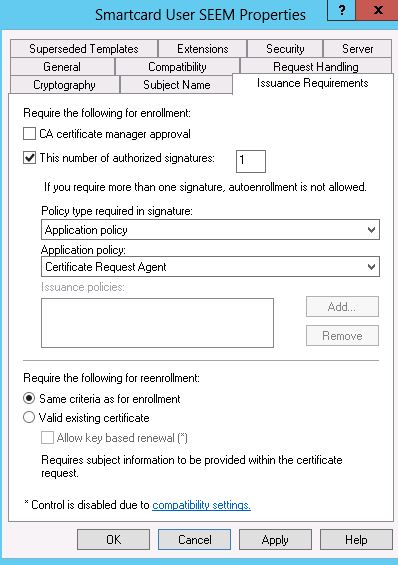
7. Ensure that the Issuance Requirements match the following settings
8. After this is done, go back to the Certificate Authority MMC. Right Click on the Certificate Templates node, Select New and then select ‘Certificate Template to Issue’ , and import the ‘Enrollment Agent’ and ‘Smartcard User SEEM’ just created
BACK to Top
3. Preparation of Safenet USB eToken for domain user authentication
0. Install the Safenet Authentication Client ver 8.2 in the windows server 2012 domain controller and the domain windows 7 client.
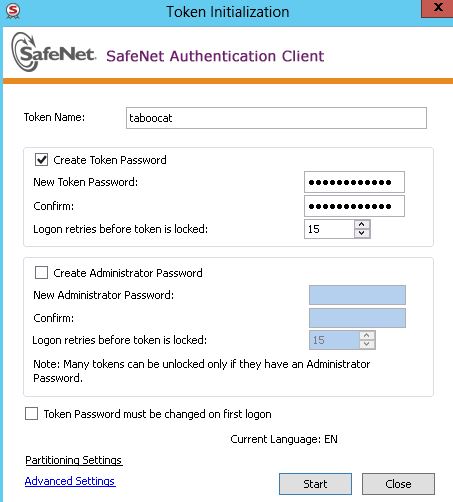
1. Run Safenet authentication client tools from any of them and then format Safenet eToken with a new password
Note:
– uncheck “Token Password must be changed on first logon”
– click “Advanced Settings” if need to change the password complexity
2. Go to Domain controller, and create a new AD user taboocat which will become the smart card user, ensure an Email address field is entered for this account in AD user properties:

BACK to Top
4. Enroll the Enrollment Agent Certificate in domain1\server02
I will set up domain1\server02 an an enrollment Station, so as to enroll new smart cards (USB eToken) on behalf of other users:
1. Launch MMC & Import the Certificates Module & Manger the certificates for ‘My User Account’”
mmc -> File -> Add/remove snapins -> Import the Certificates snap-in -> This snap-in will always manage certificates for : ‘My User Account’
2. Right Click on the ‘Personal’ Node, Select ‘All Tasks’ and then Select ‘Request New Certificate’
3. Click Next on the wizard, and then select ‘Active Directory Enrollment Policy’
4. Select the ‘Enrollment Agent’ Certificate, and then click on ‘Enroll’
5. Enroll on behalf of …
To provide new user taboocat with an USB eToken for authentication, we need to enroll taboocat user and generate a certificate which will then be imported on to the USB eToken.
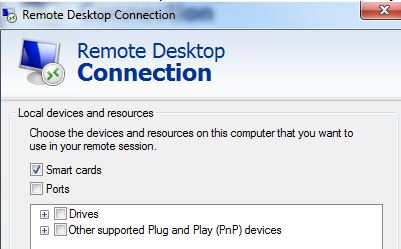
0. Logon domain1\server02 (check “smartcard” under Local devices and resources) as DOMAIN1\administrator
1. Launch MMC & Import the Certificates Module & Manger the certificates for ‘My User Account’
2. Right Click on Personal > Certificates and select All Tasks > Advanced Operations and click on ‘Enroll on behalf of…’
3. Select next on the wizard, and choose the ‘Active Directory Enrollment Policy’ and select next
4.You will now be asked to select the Signing Certificate, This is the enrollment certificate you requested earlier.

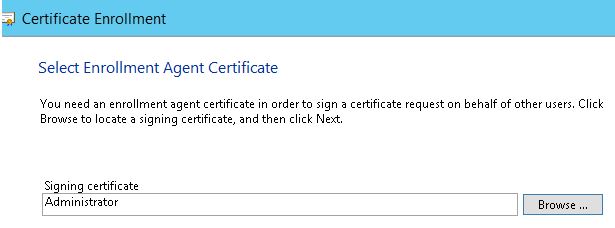
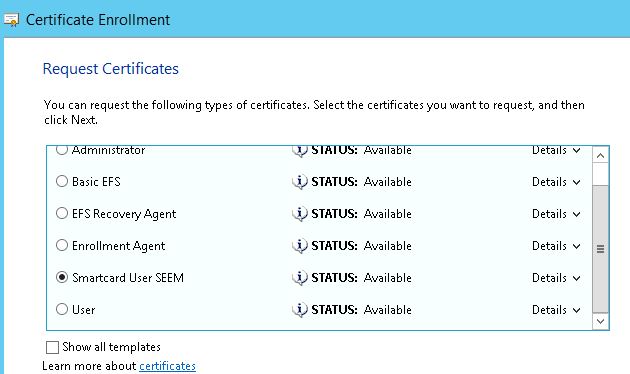
5. On the next screen, you need to select which certificate you would like to request and in this instance it will be ‘Smartcard user SEEM’ which is the Template we created earlier.
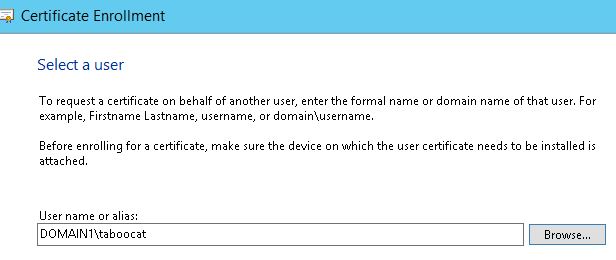
6. Next, You need to select the user you wish to enroll on behalf off. click browse and type in the username of the employee you wish to enroll. In this instance I am just going to use my Administrator Account.
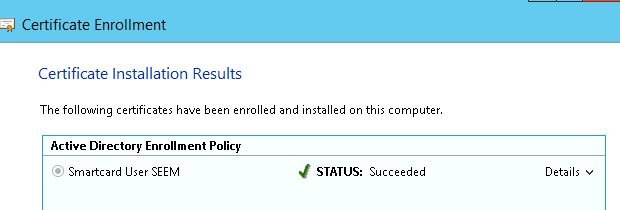
7. On the next screen, proceed with the enrollment by clicking on ‘Enroll’ where you will then be asked to insert a smartcard into your reader.

8. You will then be asked to type in the smartcard PIN number.
6. Configuration on remote desktop client (from different windows domains )
1. Install the Safenet AC Tools and drivers in remote desktop client
2. Plugin the eToken and install the domain1\taboocat’s certificate into with command “certuil -scinfo”
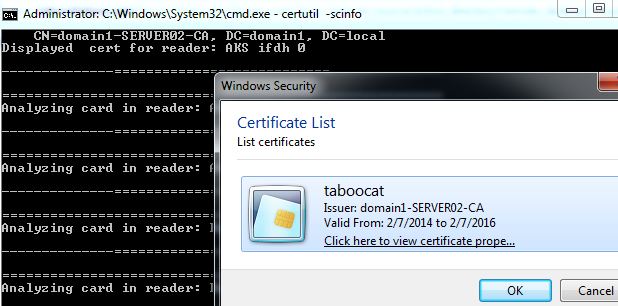
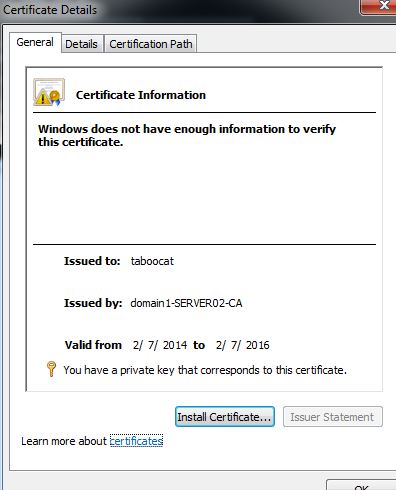
Client to view certificate and Install Certificate :
3. Update below registry in local remote desktop client so that we can be allowed to key in username hint which is required for smart card remote desktop logon when local and remote machines are of different windows domains:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\SmartCardCredentialProvider]
“AllowCertificatesWithNoEKU”=dword:00000001
“AllowSignatureOnlyKeys”=dword:00000001
“ForceReadingAllCertificates”=dword:00000001
“X509HintsNeeded”=dword:00000001
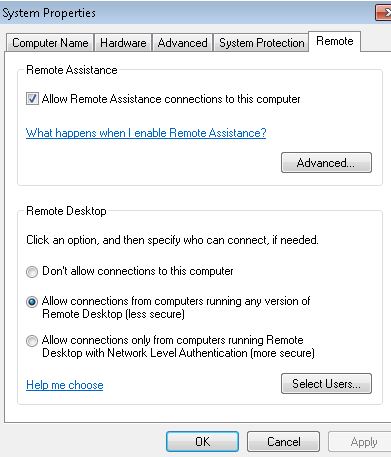
4. Now Logon domain1\client01 as administrator , ensure you **do not** use NLA authentication for it’s remote desktop access, whereas NLA does not allow use of User Name Hint :
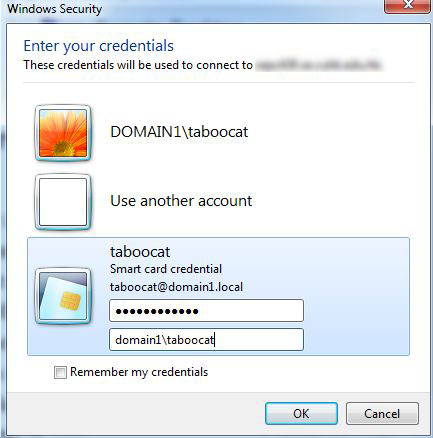
5. You may now start remote desktop (check “smartcard” under Local devices and resources) to domain1\client01 using the USB eToken ,
BACK to Top